Adding collaborators to Modernisation Platform accounts
Collaborators are defined as GitHub users which are not part of the ministryofjustice GitHub organisation.
Users who are part of the organisation are added to the platform by joining a GitHub team.
To enable collaborators to use the Modernisation Platform we need to give them the following access:
- Access to our Github repositories (if needed)
- Access to the relevant AWS accounts
- Access to be able to approve deployments (if needed)
You can request that a collaborator be added through the New Collaborator issue template.
Before you start
Have you spoken to the person who requested the new external collaborator? Have you confirmed the details in the GitHub request? Do you have contact information for the new external collaborator?
Access to our GitHub repositories
In order to create infrastructure, collaborators will need to have push permissions to the modernisation-platform-environments
repository. This will be applied through our GitHub terraform code when a collaborator has a valid github_username.
If no access to GitHub is required, setting their
github_usernametono-value-suppliedwill ensure they are not grantedpushaccess to the modernisation-platform-environments repository .
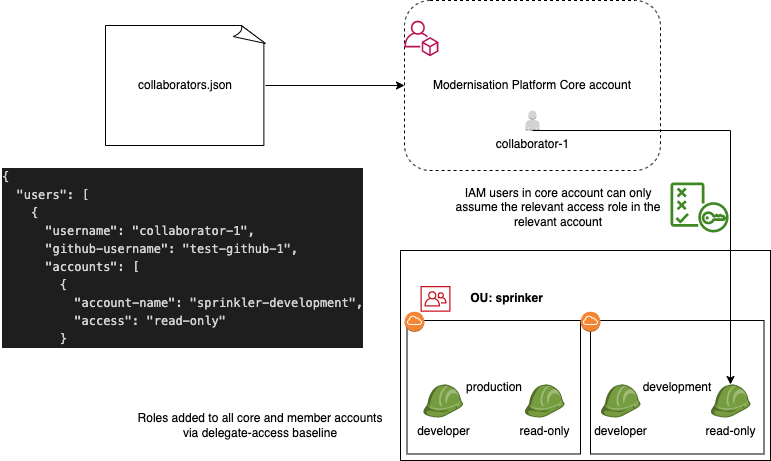
Access to the relevant AWS accounts
Add the collaborators to the collaborators.json file.
Valid access levels are detailed here.
The modernisation-platform-account-github workflow will create the users when a pull request with these changes is merged.
Due to the move of the GitHub code to a new repository, the modernisation-platform-account pipeline must be run manually to create users until we implement automation for this process.
Once their IAM user has been created, log into the AWS console yourself and:
- Switch into the superadmin role in the Modernisation Platform account.
- Go to their IAM user in IAM Users.
- Go to the Security Credentials tab.
- Configure console access with an autogenerated password (Note a user can only update their password once MFA has been enabled).
- The user will need to assign an MFA device on the first log in.
- The user will need to log out and back in to finish enabling MFA.
- The user can go to the Security Credentials tab to change the password.
Example file entries
{
"users": [
{
"username": "test-collaborator-1",
"github-username": "test-github-1",
"accounts": [
{
"account-name": "sprinkler-development",
"access": "read-only"
},
{
"account-name": "sprinkler-development",
"access": "developer"
},
{
"account-name": "testing-test",
"access": "read-only"
}
]
},
{
"username": "test-collaborator-2",
"github-username": "no-value-supplied",
"accounts": [
{
"account-name": "sprinkler-development",
"access": "read-only"
}
]
}
]
}
Diagram
Access to be able to approve deployments
The limit of the number of reviewers (teams or users) that can be added to a GitHub environment is six. Two of these spaces will be taken by the application GitHub team and by the Modernisation Platform GitHub team leaving only four spaces to add collaborators.
The deployment approver(s) should be added as ‘additional_reviewers’ specified per an environment in the application.json file (See: “additional_reviewers” in Another example for an example).
Removing collaborators
To remove collaborators reverse the above steps.
In order to remove the collaborator IAM user, the Terraform in modernisation-platform/terraform/modernisation-platform-account must be run locally as a superadmin user, as the pipelines do not have permissions to delete users. Alternatively the pipeline can be run, then when it fails delete the user and rerun the failed job.
Before proceeding, check all relevant <application>.json files for references to the collaborator in the additional_reviewers field. If the user is listed, remove their entry from each applicable file.